
Blockchain world currently struggles with a privacy issue. While there is a lot of hubbub about cryptocurrencies bringing “unrivaled safety” when it comes to protecting your personal transaction data, this isn’t exactly true. Blockchain is, by its very nature open and transparent. While you can’t look at a cryptocurrency address and see the name and personal data of its owner, anyone can use a blockchain explorer and observe what and how much that crypto address has been buying and selling. However, address ownership leaks can happen and important sensitive private data can get exposed. This doesn’t seem like that much of an issue but some (if not most) people don’t really want to have their transaction history known to everyone, for various reasons. In a hypothetical world a real owner of the address can be exposed. Alongside giving advertisers and possibly malicious people access to your purchasing data, blockchain transparency can potentially be used by various government and law enforcement agencies to track, tax and punish people for using alternative payment channels.
Bitcoin, Ethereum and many other cryptocurrencies of today suffer from these issues. Naturally, companies have noticed the need for a privacy centered token, and as a result we have a number of privacy-centric tokens and techniques that are getting more popular each day. Zcash is just one of those privacy coins and it bases its privacy-protection mechanisms on a specialized technology called zero knowledge proofs or zk-SNARKs.
What you'll learn 👉
History
The idea of zero-knowledge proofs is a brainchild of MIT researchers, namely Goldwasser, Silvio Micali and Charles Rackoff. They were working on problems related to interactive proof systems. Before discovering the zk-SNARKs technology, the assumption was that the “prover” was the malicious one in any scenario, meaning that they will be the one who will try to fool the verifier. These 3 researchers flipped the board and started questioning the morality of the verifier instead of the prover. They started by showing concern about the amount of knowledge about the prover that the verifier will get to know during the process of verification. The following question they asked was: how can we say for sure that the verifier won’t leak the acquired knowledge?
Nowadays, zero knowledge proofs technology has been directly promoted by people like Ethereum co-creator Vitalik Buterin, Christian Reitwiessner and Edward Snowden. The highly complex mathematics (so-called “moon math“) behind the zero knowledge proof technology can only be understood in its entirety if you possess Masters Degree levels of knowledge about the subject. For those willing to take on the challenge of understanding the zk-SNARKS technology, Vitalik Buterin made a couple of Medium posts relating to the subject.
Read also:
About zk-SNARKs

The acronym zk-SNARK stands for “Zero-Knowledge Succinct Non-Interactive Argument of Knowledge,” and refers to a proof construction where one can prove possession of certain information, e.g. a secret key, without revealing that information, and without any interaction between the prover and verifier. This is significantly different than other systems of proof where at least one party needs to know all the information. An example of this would be a password to someone’s account that is stored on a server.
The server has the plaintext version of your password, and your privacy is at the mercy of the server (the verifier in this scenario). If the server gets compromised or attacked, then your password will be with the malicious party and the consequences could be dire. In order to counter these scenarios, zero knowledge proofs are absolutely essential and path breaking in every sense.
A prover can, for example, take the hash of this password stored on a server and convince the verifier that there indeed exists a password with this hash value, without revealing what it is. In a zero-knowledge system the prover can convince the verifier not only that the password exists, but that they in fact know the password – again, without revealing any information about the password itself. You just knowing the password isn’t enough; the server needs to check is indeed valid so it can grant you access to password-protected contents. With zero knowledge proofs, you basically use mathematical proof to prove that you have the correct password.
The value of zk-Snarks in modern blockchain technology is clear. It smoothly integrates with the smart contract technology. A smart contract is basically an escrow of funds which gets activated once a particular function is done. When the tasks that need to be done are multi layered and confidential, problems arise. You could potentially be required to conduct multiple steps in order to receive your payment. Zk-Snarks proves that those steps have been taken in the smart contract without revealing what they actually are.. It can just reveal part of the process without showing the whole process itself and prove that you are being honest about your claims.
Let us deconstruct the zl-SNARK acronym in a bit more detail:
- Succinct – the sizes of the hash functions (proofs) are tiny in comparison to the length of the actual process required to create them.
- Non-interactive – there is no or only little interaction. For zk-SNARKs, there is usually a setup phase and after that a single point of contact between the prover and the verifier. Furthermore, SNARKs often have the so-called “public verifier” property meaning that anyone can verify without interacting anew, which is important for blockchains.
- ARguments – the verifier is only protected against computationally limited provers. Provers with enough computational power can create proofs/arguments about wrong statements. (Note that with enough computational power, any public-key encryption can be broken). This is also called “computational soundness”, as opposed to “perfect soundness”.
- of Knowledge – it is not possible for the prover to construct a proof/argument without knowing a certain so-called witness (for example the address he wants to spend from, the preimage of a hash function or the path to a certain Merkle-tree node).
If you add the zero-knowledge prefix, you also require that during the interaction the verifier learns nothing apart from the validity of the statement.
Quality zero-knowledge proofs are verifiable within milliseconds and contain only a few hundred bytes, even for statements about programs that are very large. In the initial zero-knowledge protocols the prover and verifier had to communicate back and forth for multiple rounds, but in “non-interactive” constructions, the proof consists of a single message sent from prover to verifier. Right now the zk-SNARKS system produces non-interactive, short, blockchain-viable knowledge proofs by generating common reference parameters between the provider and the verifier.
If someone had access to the secret randomness used to generate these parameters, they would be able to create false proofs that would look valid to the verifier. For Zcash, this would mean the malicious party could create counterfeit coins. To prevent this from ever happening, Zcash generated the public parameters through an elaborate, multi-party ceremony. More details about the parameter generation ceremony and the randomness behind it can be seen on the zCash Paramgen page. Another good source of information is this blog post or projects whitepaper.
Encoding
In order to have zero-knowledge privacy in Zcash, a mathematical function determines the validity of a transaction (determined the network’s consensus rules) by returning the answer of whether the transaction is valid or not, without revealing any of the information it performed the calculations on. This is done by encoding some of the network’s consensus rules in zk-SNARKs. The steps for achieving this encoding are as follows:
Computation → Arithmetic Circuit → R1CS → QAP → zk-SNARK
The first step in the process of creating a mathematical representation of the transaction validation rules is creating an “arithmetic circuit” by breaking down all the logical steps into smallest operations. Just like in a boolean circuit, where a program is compiled down into single steps like AND, OR, NOT, when a program is converted to an arithmetic circuit, it’s broken down into single steps consisting of the basic arithmetic operations of addition, subtraction, multiplication, and division.
Here is an example of what an arithmetic circuit looks like for computing the expression (a+b)*(b*c):
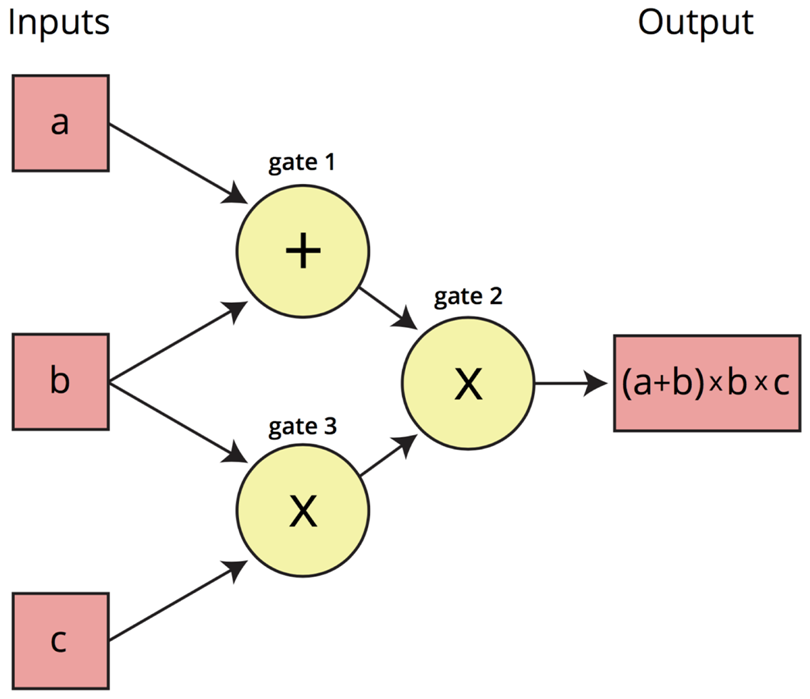
Inputs a, b, c are “traveling” left-to-right on the wires towards the output wire. A Rank 1 Constraint System, or R1CS, is required to confirm that the values are “traveling correctly”. In this example, the R1CS will confirm that the value coming out of the addition gate where a and b went in is a+b.
In this R1CS representation, the verifier has to check many constraints — one for almost every wire of the circuit. In a 2012 paper on the topic, Gennaro, Gentry, Parno and Raykova realized that it was possible to “bundle all these constraints into one”. This method uses a representation of the circuit called a Quadratic Arithmetic Program (QAP). The single constraint that needs to be checked is now between polynomials rather than between individual numbers, which would require much more time. Therefore, you only have to check that the two polynomials match at one randomly chosen point in order to correctly verify the proof with high probability.
zk-SNARKs vs other privacy protocols
Each major privacy protocol uses one form of privacy technology designed to prevent your data from being exposed. Zcash decided to go with the zk-SNARKS technology, and this has resulted in it gaining recognition from Ethereum and its developers.
The technology has impressed Vitalik and his coworkers so much that Ethereum wants to integrate ZkSnarks into its own platform. As the Metropolis phase of ETH roadmap is beginning, one of the most important plans is creating an alliance with Zcash which will include the mutual exchange of value. The chief developer of Zcash, Zooko Wilcox, held a presentation in DevCon2 in Shanghai which explored the future of such an alliance. According to him, there are 3 ways that Z-Cash and by extension, zk-SNARKs could be integrated with Ethereum.
First way is called Baby Zoe (Zoe = Zcash on Ethereum). It adds a zk-snark pre-compiler on Ethereum and makes a mini Zcash smart contract on Ethereum. The idea is to see whether the Ethereum system can create a zk-snark enabled DAPP on top of its blockchain.
The second way aims to bring Ethereum compatibility onto a zk-SNARKs based blockchain. This could potentially open up new possibilities for Zcash, like allowing it to run DAPPS or its very own virtual machine.
The third way is called Project Alchemy. This is basically the connection and interoperation of the two blockchains in a way that value can seamlessly move between the two. The way that Zcash plans to do that is by cloning the BTC Relay. It is an Ethereum script which was written to create a Bitcoin light client inside Ethereum. The Zcash clone will use the same concept to create a Zcash light client inside Ethereum.
Currently zk-SNARKs is not being used for all Ethereum transactions, and is instead only a “tool in the toolbox“.
The competition in privacy coins market has its arguments. Monero uses ring signatures while PIVX uses a zero coin protocol which involves exchanging units of PIVX for an anonymized voucher of sorts called zPIV. These vouchers can then be sent to any normal address and will be received as regular units of PIVX. While all of these have their positive and negative sides the concensus online seems to be that Zcash could offer the best solution going forward. However, it will first need to address a few issues, namely the fact that all blocks created for the first few years include a 20% “tax” that is automatically sent to the founders of the currency. This has been dubbed “the founder’s tax“.
Additionally, due to the nature of zk-SNARKs, it has been theorized that if the founders of the currency either collude or are coerced, they could potentially make an infinite number of new Zcash tokens without anyone knowing. This is because, at this time, there is no way to know the exact total supply of Zcash tokens.
Bitcoin Private
As a response to Zcash issues, recently a fork of Zcash was announced under a name Zclassic. The fork remained mostly under the radar for the majority of its existence, but has been rebranded recently under a name of Bitcoin Private.

In addition to the name change, Bitcoin Private will also make use of the original Bitcoin blockchain but with a number of changes and upgrades including the implementation of zk-SNARKs. In response to this change, prices for Zclassic exploded and went from around one dollar to nearly $100 at its peak. A snapshot of all existing ZCL and BTC holdings occurred at the hard fork. Anyone holding ZCL or BTC in a wallet or supported exchange was credited Bitcoin Private (BTCP) at a 1:1 ratio.
Conclusion
Zcash is the first widespread application of zk-SNARKs, a novel form of zero-knowledge cryptography. The strong privacy guarantee which Zcash brings stems from the fact that transactions in Zcash are protected by being fully encrypted on the blockchain and from the fact that they can still be verified as valid under the network’s consensus rules by using zk-SNARK proofs. It is a safe (if still somewhat flawed) protocol that definitely has an exciting future ahead.







