
Can blockchain be hacked?
It seems like a day cannot pass without news popping up about something getting hacked. From your grandma screaming at her Facebook for serving her an add to a phishing site which emptied her credit card to American press screaming at Russians for (allegedly and unlikely) helping elect Donald Trump become a president, hackers are running rampant all over the internet. And while cyber security keeps improving, the improvements mostly happen as a reaction to old hacks. Cyber criminals always seem to be thinking one step ahead, finding ways to break into even the safest of protocols. The overall safety isn’t helped by the fact that most of the internet rests on a dated infrastructure that is highly vulnerable to various cyber-attacks.
Enter blockchain, a seemingly new technology based on cryptography and coding which is claimed to be completely hack-proof. Looking at the technical side of the blockchain we can see it consists of blocks which are linked to eachother with various hashing algorithms. Bitcoin, the most famous cryptocurrency out there, uses SHA (Secure Hashing Algorithm) 256 for example. This cryptography ensures that no one can change any data that was previously added to the blockchain; if someone attempts to change said data, a new hash is thrown out when the data is hashed through the algorithm and the network will notice that something isn’t original. This way the entire network is responsible for the validity of the data and the blockchain; it would take an enormous amount of resources to fool it.
A Quora user CryptoniumX summed up blockchain security pretty neatly by posting the following on a question asking can blockchain be hacked:
“What makes Blockchain hack proof is the millions of users of Blockchain. They make it difficult for anyone to corrupt the network. Each block has a timestamp and a link to the previous block forming a chronological chain reinforced through cryptography, ensuring the records cannot be altered by others.”
Therefore technically, blockchains themselves are immune to hacking. However, in the past we have seen stories about various blockchain based projects suffering hacks and cyber-attacks, which proves that even the safest technology of them all can be threatened. As with any technology, blockchain has its weak points which can be exploited. It is important to note that not a single attack which happened was a result of a weak point inside the blockchain itself giving way but rather a result of human error or outside technical vulnerability. So according to these points of entry which hackers can use to endanger blockchain-based networks, we can make a distinction between various types of attacks:
- Sybil Attack
Relatively rarely mentioned attack that could make a lot of damage to a cryptocurrency is a Sybil attack. The attack consists of an attacker flooding the network with nodes he controls.
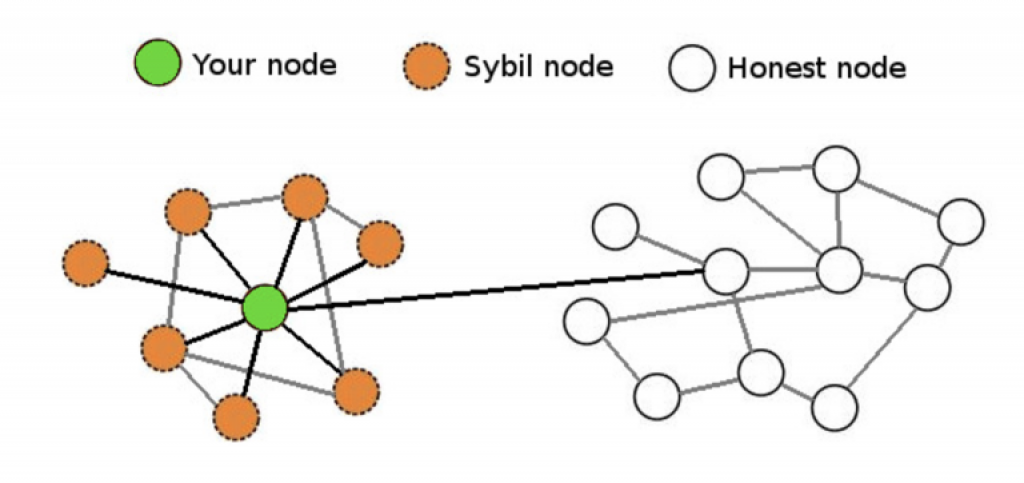
Source: https://www.coindesk.com/bitcoins-security-model-deep-dive/
In a certain scenario, a regular, unsuspecting node could end up connected only to negative nodes. This would render the node isolated from the “good” network, meaning that the attacker could exploit said node in several ways:
- the attacker can refuse to relay blocks and transactions from everyone, effectively disconnecting the node from the network
- the attacker can relay only blocks that they create, effectively putting the node on a separate network and then also leaving it open to double-spending attacks
- if the node relies on transactions with 0 confirmations, the attacker can just filter out certain transactions to execute double-spending attacks
Such an attack has never happened before in the cryptocurrency world and Bitcoin was intentionally created as being resistant to them. Sybil attacks are avoided in Bitcoin by requiring block generation ability to be proportional to computational power available through the proof-of-work mechanism. That way, an adversary is limited in how many blocks they can produce. This provides strong cryptographic guarantees of Sybil resilience.
- DDoS Attack
A DDoS attack is an attack where malicious players overload a server by flooding it with massive amounts of traffic. An attack commonly seen online, DDoS has been used in various occasions, from people looking to pull a prank on a twitch streamer to large groups of hackers looking to cause much bigger mischief.
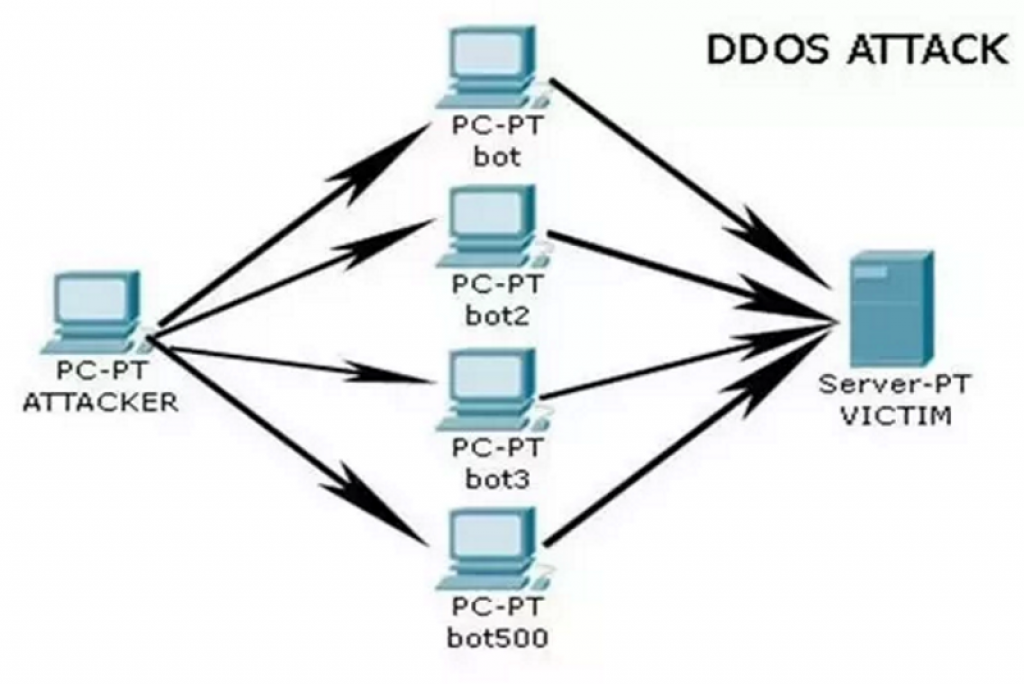
DDoS attacks work as pictured above. An organizer (hacker) instructs an army of bot/zombie PC’s to send huge amounts of traffic to a server over a continuous period of time. As a result, the server becomes overloaded with requests to access the website it’s responsible for; this either leaves legitimate requests waiting for a long time to become processed or crashes the entire server, leaving it unable to process anything.
As for the crypto world, DDoS attacks consist of sending massive amounts of small and invalid transactions, in an attempt to overload the network nodes and slow down the processing of real transactions. Cryptocurrencies like Bitcoin are being threatened by DDoS attacks all the time; however, Bitcoin designers were aware of the potential issues with these attacks (as they were pretty popular at the time) and have implemented measures which ensure that such attacks cannot harm the network. Performing a DDoS attack on the Bitcoin network would be extremely difficult now, as it has thousands of active nodes keeping its mempool (pool of transactions) working. Even if such an attack were successful, it wouldn’t allow hackers to compromise the security of funds; it would only cause a slight annoyance by slowing the network down for a while.
Bitcoin experienced issues with DDoS attacks in the past, most notably between 2015 and 2017. Coinwallet.eu famously arranged a stress test for the cryptocurrency by launching a DDoS attack on its nodes. This was done amidst the ongoing debate about increasing the size of Bitcoin blocks. The attack was meant to prove that an increase in block size would help improve Bitcoin network’s ability to defend from such attacks in the future. Sometime later, a huge attack which launched over 80000 instant insignificant transactions was launched by an unknown player. This overloaded the Bitcoin mempool significantly and the network was saved mostly because F2Pool, a massive mining pool at the time (doesn’t exist anymore) took on the responsibility of cleaning out the clutter. They stuffed the entire 80000 transactions into a single block and brought the mempool to its normal state.
While the network has experienced smaller DDoS attacks, these were never that big in scale and were never taken seriously by the mining pools until May of 2016, when the amount of accepted spam transactions rapidly increased. This caused a network congestion and real transactions suffered. As the talk of increasing Bitcoin block size was rampant at the time, many people suggested that mining pools are supporting this notion and are deliberately slowing the network down by mining junk. Since then, the transaction congestion has been dealt with and the network is back to its usual throughput.
As said before, DDoS attacks aren’t able to endanger user funds. However, they are able to endanger the ability of Bitcoin based services to function. DDoS mitigation firm Imperva Incapsula claimed at the tail end of 2017 how digital currency sector is among top 10 most targeted with DDoS attacks. These attacks are most of the times ordered by Bitcoin business operators themselves; DDoSing a market competitor puts him out of business and sends users willing to transact crypto your way.
- 51% Attack

One of the most dreaded phrases in the crypto world is the phrase 51% attack. If more than half of the processing power on a blockchain fell into the hands of a single malicious entity — which could be one person controlling a number of nodes, or a group of hackers working together — it could prove very destructive for the other, well-intentioned members of the network. Being in such position would let him mine blocks faster than the rest of the network and enable him to start “double-spending”. Double spending in crypto is a practice where a transaction is added to the blockchain and after the thing that was paid for by cryptocurrency is received, the double-spender uses it superb hash-power to remove the transaction from the blockchain. The coins that were spent are back in the double-spenders wallet, allowing him to double spend.
This attack doesn’t allow the attacker to create coins from nothing; the only advantage he gets is the ability to spend what he owns more than once. Most of the times this attack is mentioned as being aimed not at lining ones pockets but rather at bringing the reputation and price of attacked coin down. 51% percent attacks are extremely hard to do, as resources which one would require to gain control of 51% of Bitcoin’s mining pool would be astronomically expensive and difficult to maintain by a single entity. The attacker would be much better off to simply spend the hash rate to mine for Bitcoin instead of trying to pull off a 51% attack.
In the past, we have seen 51% attack happen against smaller blockchains and networks. A group of hackers calling themselves “51 crew” attacked blockchain projects Shift and Krypton. The attackers asked for Bitcoin to be paid as ransom while claiming their intentions were not to kill these projects. Ultimately both projects refused to “negotiate with terrorists” and were punished by having their chains hard-forked. Since then, Krypton went under and Shift is still present on the market in small volume. Just recently,
Verge recently suffered a 51% attack as well, when a malicious miner gained control of over half of the coin’s hashrate and started mining coins rapidly. Using a number of exploits in the XVG code, the attacker was able to mine multiple blocks one second apart, all performed using the Scrypt algorithm, a feat which ought to have been impossible. Over 250 thousand coins stolen and one accidental fork of the Verge blockchain later, Verge development team managed to regain control of their coin.
To protect their networks from 51% attacks, developers are turning to a so called proof of stake consensus, where the ability to verify transactions is determined by the stake a verifier has in the network. In such consensus, the stake holders are at the same time in charge of verification; as they are the biggest holders of the coin they are verifying, they clearly have an interest in behaving in a non-malicious way.
- Routing attack
While Bitcoin nodes are pretty decentralized across the world, the number of ISP’s which service them is relatively limited. A research done by ETHZurich suggests that 30% of the Bitcoin network is having its nodes hosted by 13 different ISP’s. At the same time, over 60% of total traffic towards Bitcoin nodes is handled by a grand total of 3 ISP’s. If one or more of these ISP’s were compromised, the entire Bitcoin network could take a massive hit.
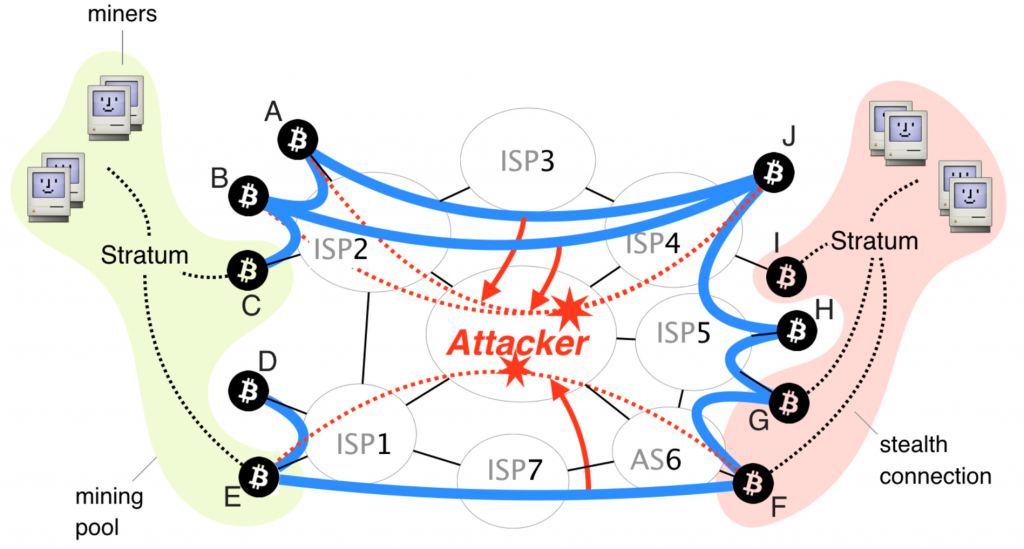
Besides delaying block delivery, routing attacks could open the doors for malicious players to double spend. This attack would work by splitting the entire network into two separate parts. By routing traffic, attacker can prevent the nodes on one side from communicating with nodes on the other side, which can result in the creation of parallel blockchains. An attacker could then double spend on a blockchain that is shorter. Once his goods arrive, he can stop rerouting traffic; when this happens, the network will detect two blockchains. The shorter chain, which contains attacker’s transactions, will be refused by the network, returning every coin he spent back into his wallet.
- Human error
Previously mentioned attacks were outside attacks focused on slowing the network down and double spending. Any quality blockchain supported network will absorb these attacks with relative ease and won’t suffer long as a result of them happening. However, the most important way off attacking the network comes from the inside. Humans that are in charge of creating, running and maintaining the blockchain network are the leading source of said networks vulnerabilities.
The most well-known example of a human error is the hacking of DAO.
DAO (or Decentralized Autonomous Organization) was envisioned as a code-controlled, Ethereum based organization designed to give anyone the power to invest in it and vote on projects they want the DAO to support. A so called “Split mechanism” was built into DAO which allowed users to pull out their Ethereum and give their DAO tokens back in return at any time. It consisted of two steps:
- Return the Ethereum to the token holder
- Take the tokens back and register the transaction on the DAO blockchain
A hacker found an exploit in the code which allowed him to repeat the first step without moving onto the second, and by the time he was shut down he managed to extract 50 million dollars worth of Ethereum out of the DAO. Ethereum community went livid and in response a soft-fork to recover the lost funds was requested to erase the DAO hack from the blockchain. However this could not be done with a simple soft fork and as a result of a community splitting whether the hack should be reversed or not a hard fork was made and original Ethereum split into two blockchains: Ethereum Classic (ETC), which continued on the blockchain that had the DAO hack, and Ethereum (ETH), which had the DAO hack removed from the blockchain.
Another source of human error is the inability to stick to security protocols set in place to protect the blockchain form getting hacked. Many an exchange ended up being hacked as a result of malpractice, sloppy employee behavior leading to phishing attacks and important data getting stolen. Also, keeping hold of private keys is the single most important task that a user/exchange needs to do; we have seen hundreds of millions of dollars being lost as a result of their inability to do so. The Bitfinex hack, the Mt. Gox hack, the BitGrail hack and every individual user hack so far could have been prevented if proper safety and work protocols were followed.
Final thoughts
Blockchain technology is very simple, yet extremely secure. However it is still very new and some high profile mistakes and problems with using it are bound to happen. Every new digital technology goes through those initial pains of having software defects and having people trying to hack it. These pains are only temporary and they lead to overall improvements in the technology and implementation of good practices. This should not deter firms and developers from taking the blockchain pill. The technology and practices around it will only get better, faster and safer in the future and anyone caught lagging behind might miss out on a lot.







Great article, thank you! The latter part about ‘human errors’ for the DAO hack, I think you mean faulty code rather than effective human errors (that you mention for the exchanges)?