When original Bitcoin white paper was introduced in 2009, a document which created the roadmap and social contract for Bitcoin, many believed that it was anonymous. There is a section in the white paper on the privacy where it says that privacy can be maintained by breaking the flow of information in another place: by keeping public keys anonymous. The public can see that someone is sending an amount to someone else, but without information linking the transaction to anyone. There is also an additional firewall, where it is required to use a new key pair for each transaction to keep them from being linked to a common owner.
Besides providing the movement of funds around the world without a third party, other key and popular feature of Bitcoin was that it provided anonymity for its users. The users could move money without revealing who their identity. Or at least the users thought so.
In August 2017, the Daily Beast announced a report that Internal Revenue Service has purchased specialist software to track those using Bitcoin, according to a contract they managed to obtain.
It shows that legal authorities are not only concerned by criminal activities associated with Bitcoin, but also with persons using Bitcoin to hide their wealth and avoid paying taxes.
The obtained contract states that the purpose of this acquisition is to help IRS trace the movement of money through the Bitcoin economy. The contract was signed with Chainalysis, a company offering its „Reactor“ tool to visualize, track and analyze Bitcoin transactions. Chainalysis’ users include law enforcement agencies, banks, and regulatory entities.

The software can follow Bitcoin as it moves from one wallet to another, and eventually to an exchange where the Bitcoin user will likely cash out into dollars or another currency. This is the point law enforcement could issue a subpoena to the exchange and figure out who is really behind the Bitcoin.
Due to the fact that Bitcoin is in no rush to address this issue, as they have bigger issues with scalability, people started developing new cryptocurrencies that are claiming to be truly anonymous and fully private.
You might also consider using VPN as an additional layer of privacy protection when buying crypto.
Here are 10 cryptocurrencies that have potential to be fully anonymous.
What you'll learn 👉
Anonymous cryptocurrencies
Anonymity means “without a name” or “namelessness”. In colloquial use, “anonymous” is used to describe situations where the acting person’s name is unknown. The important idea here is that a person be non-identifiable, unreachable, or untraceable. Anonymity is seen as a technique, or a way of realizing, a certain other values, such as privacy, or liberty.
-
Monero
According to their web site, Monero is the leading cryptocurrency with a focus on private and censorship-resistant transactions. Bitcoin and Ethereum are using transparent blockchains which means that transactions are easily traceable. Sending and receiving addresses for these transactions may potentially be linkable to a person’s real-world identity. But Monero uses cryptography to shield sending and receiving addresses, as well as transacted amounts.

In order to remain private, Monero uses ring signatures, ring confidential transactions, and undetectable addresses to hide the origins, amounts, and destinations of all transactions.
Monero is also fungible or interchangeable, because it is private by default. Units of Monero cannot be blacklisted by vendors or exchanges, because Monero previous transactions cannot be connected.
-
Komodo
Komodo has powerful privacy features built into their platform. It allows the investor to trade and purchase goods and services within their right to privacy. It also allows the entrepreneur to release their product, and to crowd source funds, from an audience that may prefer to maintain this privacy.
Komodo uses KMD as the native cryptocurrency which enables users to conduct both transparent and private transactions. KMD is a fork of Zcash15 and as such KMD retained the same privacy features. Most important of these are the Zcash parameters and zk-SNARK technology. These enable users to move funds on a public blockchain without leaving a data trail for later analysis.
They claim that this is one of the most powerful forms of blockchain privacy in existence, as the provided privacy is effectively permanent. The Zcash parameters and zk-SNARK technology provide the initial foundation for users to take transparent KMD funding and make it anonymous without leaving behind a cryptocurrency trail. The Zcash project itself is a fork of Bitcoin. Thus, all the features designed by Satoshi Nakamoto in the Bitcoin protocol are also available in Komodo.
-
Dash
Key privacy feature offered by Dash is PrivateSend. It provides you with full privacy by concealing the origins of your funds. It is innovative process where your inputs are mixed with the inputs of two other people. During the process your coins do not leave your wallet meaning that you have the control of your funds constantly.

PrivateSend process starts by breaking your transaction into smaller denominations such as 0.01 Dash, 0.1 DASH, 1 DASH and 10 DASH. Then masternodes, specially configured software nodes on the network, are informed that you are interested in mixing a certain denomination. The masternodes will never know who you are.
Mixing starts when two other people send mixing requests with same denomination. The masternode mixes up the inputs and instructs all three users’ wallets to pay the now-transformed input back to themselves. Your wallet pays that denomination directly to itself, but in a different address (called a change address).
If you want to conceal your funds further, you will need to repeat the process. Multi repetition of the process makes determining your funds origins more difficult.
The process is done in the background and there is no need for your participation. If you want to make a transaction, your funds are already anonymized and there is no need for waiting.
-
Zcash
According to their web site, Zcash (ZEC) is the first open, permissionless cryptocurrency that can fully protect the privacy of transactions using zero-knowledge cryptography.
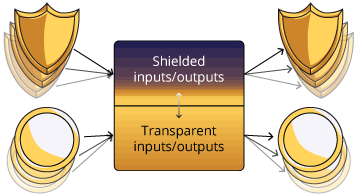
Zcash, by using uses a zero-knowledge proof construction called a zk-SNARK, enables users to send public payments that are similar to the Bitcoin. But users can choose between shielded and transparent addresses and choose to send Zcash privately or publicly. For instance, if you send Zcash from a shielded address to a transparent address, amount received will be revealed. If the payment is made from transparent address to a shielded address, amount received will be protected.
-
Zcoin
It is important not mix Zcoin with Zcash. They have common author of respective white papers and both use zero knowledge proofs, but otherwise there is no relation between the two projects.
By using zero knowledge proofs, Zcoin completely breaks the transaction links between coins. Basically, a zero knowledge proof is a proof you did something or know something without revealing any other information other than you did it. For example, proving that you know a password without actually revealing the password.

Zcoin works by allowing you to burn coins up (otherwise known as Zcoin mint) and then later redeem an equivalent number of brand new coins (known as a Zcoin spend). These coins appear with no prior transaction history and are similar to newly mined coins. The zk-proof is used to prove that you indeed burnt coins without revealing the specific coins that you burnt and therefore are entitled to redeem an equivalent number of new clean coins.
-
Verge
Verge uses multiple anonymity-centric networks such as TOR and I2P. The IP addresses of the users are fully obfuscated and transactions are completely untraceable.

TOR, short for the original software project name “The Onion Router”, is an IP obfuscation service which enables anonymous communication across a layered circuit based network. I2P is a highly obfuscated tunneling service using ipv6 that anonymizes all Verge data being sent over the network.
But most notable feature of Verge is Wraith Protocol. It enables users to choose from public and private ledgers on the Verge blockchain. If the Wraith Protocol is ON, your transaction is linked to stealth address and cannot be seen through the blockchain explorer. If it is OFF, your transactions are linked to public address and are visible through the blockchain explorer.
-
Bitcoin Private
Bitcoin Private is a “fork-merge” of Bitcoin and Zclassic and is intended to add privacy and spendability to the Bitcoin blockchain while remaining cognizant of the challenges, choices, and failures of prior forks.

For the purpose of privacy, Bitcoin Private is using zk-snarks technology, just like Zcash. It means that payments are published on a public blockchain, but the sender, recipient and other transaction data are anonymous.
Users can make transactions transparent or shielded. Transparent transactions are same as Bitcoin transactions where all transaction data is stored on the blockchain. On the other hand, data of the shielded transactions are encrypted into special section of a block called the JoinSplit, which are verifiable but indecipherable to third parties.
Shielded transactions, conversely, encrypt these details into a special section of a block called the JoinSplit. These transactions are verifiable but indecipherable to 6 third-party observers.
-
Spectrecoin
Spectrecoin (XSPEC) is an innovative privacy focused cryptocurrency, featuring an energy-efficient proof-of-stake algorithm that provides rapid transaction confirmations, ring signatures for privacy and anonymity, and a fully integrated TOR and OBFS4 layer for IP obfuscation within the wallet.
Users cannot connect to the Spectrecoin network without TOR and all nodes have hidden service address. Network participants know only their own IP address.
Spectrecoin has also integrated support for OBFS4, which is an obfuscation protocol that hides the nature of the traffic that goes through it. With OBFS4, it is possible to use Spectrecoin even in countries where access to the TOR network is censored, like China or Iran. In short, the integration of OBFS4 effectively ‘wraps’ the TOR traffic in another layer making it appear as normal internet traffic.
Spectrecoin is the only privacy coin to offer this feature.
-
PIVX
PIVX was created to provide users with a viable currency that preserves individuals’ privacy and security. It is the first Proof of Stake coin with the Zerocoin protocol (called zPIV) and Zerocoin staking (named zPOS); a completely new Proof of Stake algorithm providing unparalleled privacy, speed of transactions, and low transaction costs.

zPIV provides coin mixing service using zero knowledge proofs to cut off the link between the sender and the receiver with 100% anonymity and untraceability. This means that each coin that gets sent using zPIV is now 100% fungible as it has no determinable history attached to them.
When a user’s wants to send some zPIV amount to a PIVX address, his wallet sends a zero-knowledge proof to the blockchain that allows the zPIV to be converted back to PIV and sent to the target address all in a single step.
Since zPiv spending creates brand new coins, if a spender can provide zero-knowledge proof that she has coins in the accumulated pool, the coin’s transaction history from its previously associated addresses become unlinked and thus results in an untraceable transaction.
-
NavCoin
NavCoin is based on Bitcoin but with additional benefits such as faster transactions and low electricity usage. Unlike Bitcoin, NavCoin is using Proof of Stake algorithm to secure the network.

In order to support private transactions, they have created a separated blockchain and software platform on top of the NavCoin protocol and is called NavTech. Users are able to choose to encrypt transaction data that is to be sent via NavTech blockchain and in process cutting off the link between the two addresses.
NavTech private payments are based on RSA, which is a widely used and studied algorithm. It currently uses 2048 bit length keys which are nowadays considered safe.
Conclusion
The general concern among legal authorities is that anonymous coins can be used for illegal activities, such as forbidden substances or money laundering. The famous case of FBI’s investigation on the infamous anonymous marketplace Silk Road, proved that Bitcoin was used for illegal activities.
Due to the misuse of the digital money, there is general opinion that privacy currencies are illegal. Privacy coins are perfectly legal.
For instance, US Senate considers virtual currency as legal means of exchange since 2013, as well as decentralized payment systems. In other countries such as United Kingdom, it is permitted to use digital currencies but are subject to value added tax (VAT). The EU is yet to regulate the crypto market.
Here is a comparison of privacy focused coins – first appeared on Reddit.
Comparison:
Monero (XMR) vs. Bitcoin (BTC) vs. Zcash (ZEC) vs. Dash (DASH) vs. Verge (XVG)
This comparison chart between Monero, Bitcoin and the largest so-called “privacy coins” strives to be unbiased and wholly factual.
If you believe there is information worth correcting, please send a message here.
| Terms | Criteria |
|---|---|
| Private | The amount of coins you own, send and receive are not observable on the Blockchain. There should be no “rich list” (a list of the largest coin holders). |
| Untraceable/Unlinkable | The coins you send and receive are not traceable (to or from), nor linkable by way of transaction history. |
| Fungible | Every coin is worth the same value and is thus mutually interchangeable. No coin risks potential blacklisting nor devaluement due to deprecating transaction history. |
| Decentralized | All nodes have equal power and control; there are no nodes that have more influence than others, i.e. masternodes. The currency is not created, maintained nor represented by any one person or company, i.e. a central authority. |
| ✓ | X | ? |
|---|---|---|
| Pass | Fail | Questionable (Read Below) |
| Private | Untraceable/Unlinkable | Fungible | Decentralized | |
|---|---|---|---|---|
| Monero (XMR) | ✓ | ✓ | ✓ | ✓ |
| Bitcoin (BTC) | X | X | X | ✓ |
| Zcash (ZEC) | ? | ? | X | X |
| Dash (DASH) | X | X | X | X |
| Verge (XVG) | X | X | X | ✓ |
- Privacy, Traceability, Linkability
Monero is cryptographically private by default, utilizing several privacy features – most prominently being stealth addresses and ring confidential transactions (RingCT).
A recipient is able to receive multiple payments through a single address, while at the same time ensuring there are no links on the blockchain between their address and anybody else’s address. This is made possible by stealth addresses, where a random one-time address is automatically created for each transaction being made by the sender. In other words, all payments sent to the recipient are routed to unique addresses on the blockchain, which in turn prevents any links – masking the recipient, and providing no way to see if anybody else has sent coins to the recipient.
While stealth addresses prevent linkability on the blockchain, when and where the coins are then moved by the recipient (if ever), is able to be traced by the original sender of the coins, by identifying outputs on the blockchain. This issue of traceability is solved by the utilization of ring signatures. With ring signatures, outputs are masked, so the sender is not able to tell if it’s their coins that are then moved by the recipient, ultimately providing untraceability. This is done by grouping the transaction being sent, with other transactions from the blockchain, to obfuscate the outputs being spent and allowing for plausible deniability.
On January 2017, Monero implemented ring confidential transactions (RingCT), introducing an improved version of ring signatures, and combining with the improvements, confidential transactions – a cryptographic tool that conceals the amount being transacted, while still allowing for the network to verify the amount without having to reveal any actual details. “Confidential Transactions include a cryptographic proof that the sum of the input amounts is the same as the sum of the output amounts, without revealing the actual numbers.” Source.
The Monero Project is currently developing Kovri, a C++ implementation of the I2P network. Kovri will allow for an extra layer of security and privacy, most importantly being the disassociation of IP addresses from transactions, among many other things. Kovri is currently in development and is coming soon.
With stealth addresses, the recipient is masked and linkability is prevented. With ring signatures, outputs are masked, so the sender is not able to trace when and where the coins they have sent to the recipient are further moved to – obfuscating traceability and providing plausible deniability. With RingCT (i.e. confidential transactions), the amount being transacted is cryptographically concealed, while still allowing for the network to verify the amount without having to reveal any actual details. With Kovri, a user’s IP address is masked and thus not associated with their transaction.
Although Monero is private by default, transactors are afforded the option of selective transparency, where a user can decide who is able to view their hidden balance by sharing their view key. Monero is private by default and optionally semi-transparent, affording a transactor the choice to prove their payment or to allow for the divulgence of their balance with a key.
- Fungibility
Because of Monero’s cryptographic privacy, untraceability and unlinkability features, coins avoid the potential of being tainted by deprecating transaction history. There is no risk of blacklisting nor devaluement of Monero, therefore all coins are worth the same value and are mutually interchangeable.
- Decentralization
Monero is truly decentralized and led by volunteer work. Developers are funded by user contribution through the Forum Funding System. Development decisions are open to public discussion, and developer meeting logs are published in their entirety for all to read. The Monero Project’s source code and all changes are available on the official Monero GitHub.
- Privacy, Traceability, Linkability
Bitcoin does not offer privacy and has never claimed to do so. The Bitcoin blockchain is completely transparent; every transaction, its history, and the amount being sent or received is public and easily viewable by an observer. Thus, Bitcoin transactions are easy to trace and link. Although your Bitcoin address is “anonymous” in that no identifying information (e.g. name, address, etc.) is attached to it, it is presumed that at some point you will cash out your Bitcoins (e.g. through an exchange) or you will purchase an item with your Bitcoins (e.g. from a merchant), and you will at that point risk connecting your identity to your Bitcoin address(es), your Bitcoins, and their entire transaction history.
- Fungibility
Not all Bitcoins are worth the same value. Due to Bitcoin’s transparent blockchain, the transaction history connected to your Bitcoin is liable to devalue it. Although it would require a substantial amount of power to deny or blacklist your Bitcoin (and all addresses associated with it, regardless of whether or not you are innocent), there have already been cases where exchanges have “blacklisted” Bitcoins and the addresses associated with them:
“As of today, we have taken measures to blacklist all addresses associated with the WannaCry attackers that are known to the ShapeShift team, as is our policy for any transactions we deem breach our terms of service. We are closely watching the situation as it continues to unfold as to block any further addresses associated,” the spokesperson added. Source.
- Decentralization
Bitcoin is decentralized. Notably, it is the first decentralized peer-to-peer payment network.
- Privacy, Traceability, Linkability
Zcash uses a new method of cryptographic privacy called “zk-SNARKs” (zero-knowledge Succinct Non-interactive ARgument of Knowledge). At the basic level, zero-knowledge proofs allow for a way to prove that the information you are sending to the other party (e.g. the amount of funds) is true, without having to broadcast said information besides the fact that it is true. In other words, “you can verify the correctness of computations without having to execute them and you will not even learn what was executed – just that it was done correctly.” Source. The cryptography behind zk-SNARKs allow for all transaction data to be private and encrypted – “Instead of publicly demonstrating spend-authority and transaction values, the transaction metadata is encrypted.” Source.
Although Zcash’s privacy components on the cryptographic level raise no doubts (even though zk-SNARKs are a fairly recent development and lack peer review), there are other concerns regarding Zcash’s handling of privacy that are worth examination. Zcash offers the choice of optional privacy. In other words, privacy (“shielding”) is not on by default. According to Zcash’s blockchain, as of writing, only an approximate 5.05% of funds are held in z-addresses (private addresses utilizing zero-knowledge proofs to ensure privacy) – on the contrary, a majority of Zcash transactions are not private, and are easily viewable by an observer. According to Zcash’s usage statistics, as of writing, in the past month, only ~500 transactions have opted to be “fully shielded” – masking the recipient, sender and the amount being transacted on a comparable level to Monero’s default transaction privacy. Out of ~148541 transparent transactions, and ~20818 partially-shielded transactions, only a total of ~0.3% of transactions within the past month have utilized the optional “full shielding” feature that is tantamount to Monero’s default privacy features.
Zcash is not “private by default” particularly due to the inefficiency of zk-SNARKs. The process of creating a transaction with zero-knowledge proofs (zk-SNARKs) is slow and costly – requiring that you run a full node, while demanding up to 4GB of RAM “for a minute or two” until the transaction is sent. Source. It is also the case that, because a majority of the blockchain is transparent, those who do use the privacy features stand out, and there may be the potential risk for an attacker to “isolate the few users who are using the privacy features. In Bitcoin, transactions appear suspicious if mixing services are used. For ZCash, this is basically the same story. For Monero, few transactions appear suspicious because they all look similar.” Source.
This information, however, is rejected by proponents of Zcash. One of the arguments brought up against the claim that “Zcash is not private by default” is that, supposedly, “the first thing that must be done before [a] block reward can be spent is [that] the ZEC must be sent to a private address. It is coded that way and cannot be bypassed, that is the very definition of ‘default’ [privacy].” Proponents even reject the “only less than 10% of Zcash transactions are private” claim, by arguing that “23% of all network transactions are shielded.” Source. These arguments, however, are misleading. In a presentation at Coinbase, Bitcoin Core Developer Greg Maxwell has stated:
“Zcash couldn’t plausibly make the private transactions mandatory, so they’re optional, and as a result, very few of the transactions in the Zcash chain actually use the private transaction feature. If you just look at the raw numbers, it’s 24%, but that number is a bit misleading, because miners are required to pay to a private address – but most miners are mining pools, and the mining pools immediately unblind those coins, and if you sort of separate out the mining load, then maybe it’s in the order of 4% of Zcash transactions are private. And as a result, that anonymity set that this ‘perfect’ anonymity system is achieving, isn’t really all that good. I think it’s a cool thing, and I’m really glad that people are trying it out, but it’s not the kind of proposal I’d want to take to something like Bitcoin today.” Source.
Because of Zcash’s overwhelmingly transparent blockchain, “It is thus possible to correlate transactions when a transparent address sends a given amount to a shielded address and later that amount is transferred to a transparent address. What was private can now be inferred through indirect knowledge thanks to knowing the ‘inputs and outputs.'” Source.
Matthew Green, author of Zerocoin – whose protocol was then improved and transformed into Zerocash, which gave birth to the currency we know today as Zcash – is a current team member at Zcash. He has previously stated, “Zerocoin would give you this incredible privacy guarantee, then we could add on some features which let the police, for instance, to be able to track money laundering. A back door.” Source.
- Fungibility
Because the blockchain and its transactions are not private by default, there is the potential, similar to Bitcoin, for an entity to deny or blacklist Zcash. This means that Zcash is not fungible, even if you “mix” the coins by way of sending it to a shielded address and then to a transparent address. As cited above, “It is thus possible to correlate transactions when a transparent address sends a given amount to a shielded address and later that amount is transferred to a transparent address. What was private can now be inferred through indirect knowledge thanks to knowing the ‘inputs and outputs.'” Source.
- Decentralization
Zcash is run by a US-based, for-profit company, the Zerocoin Electric Coin Company Source. It is head by a CEO, and numerous investors. Source.
The company takes 20% of all coins mined for the first four years as a “founders reward” – “distributed to the stakeholders in the Zcash Company — [the] founders, investors, employees, and advisors.” With 50 coins being generated every 10 minutes for the first four years, an approximate 10,512,000 coins will be created, with the founders owning 2,102,400 (20%) of what is in circulation. After those first four years, coin generation will be reduced to 25 coins per 10 minutes, and only then will miners receive 100% of what is mined. Once the cap of 21,000,000 coins is reached, the “founders, investors, employees, and advisors” can potentially own up to approximately 10% of all coins in circulation. Source.
The Zcash company (i.e. the Zerocoin Electric Coin Company, based on the original project, Zerocoin, that conceded the Zerocash protocol, which then yielded the Zcash currency) was sponsored by several corporate entities and sectors of government, notably being the U.S. Defense Advanced Research Projects Agency (DARPA), the Air Force Research Laboratory (AFRL), the Israeli Centers of Research Excellence I-CORE program, and the Israeli Ministry of Science and Technology. Source.
Zcash was launched by way of something called the “multi-party computation” – also known as a “trusted setup.” “The public parameters (zk-SNARK providing and verifying keys)” for Zcash’s launch were constructed in a ceremony spearheaded by six individuals:
- Andrew Miller (Zcash advisor)
- Peter Van Valkenberg (Zcash “board member” Source.)
- John Dobbertin (pseudonym, “The identity of ‘John Dobbertin’ has not yet been revealed, and I don’t yet know when John and I will be ready to do that.” Source.)
- Zooko Wilcox (Zcash founder, CEO)
- Derek Hinch (NCC Group, a cyber security consulting group)
- Peter Todd (Bitcoin Core Developer)
“The ceremony used a multi-party computation protocol with the property that the resulting parameters are secure unless all of the participants were dishonest or compromised during the ceremony.” Source.
“The Zcash protocol needs a special trusted setup phase for technical reasons. The secret key (“cryptographic toxic waste”) generated during this phase can be used to steal money – currently in the form of creating counterfeit coins, stealing from everyone collectively. For the secret key to leak, all six participants need to collude or be compromised. Emphasis on the latter: there are a lot of ways that the participants could be compromised against their will.” Source.
In short, there is the potential risk – if all six participants of the trusted setup were to collude – that would enable them to generate an unlimited, undetectable amount of coins. Along with this concern, with Zcash, “the total number of coins in circulation is not guaranteed from the outset, and it may not be possible to know how many there are.” Source. Nick Szabo, father of smart contracts, stated long ago that “trusted third parties are security holes.” Source. There is no way to audit Zcash to ensure whether or not the trusted setup has failed, will ever fail in the future, or was compromised from the start. The trusted setup “multi-party computation ceremony” took place between October 21-23, 2016. Source.
On November 1, 2016, Peter Todd, a Bitcoin Core Developer and one of the six individuals who participated in Zcash’s trusted setup, stated:
Let’s be 100% clear: the @zcashco trusted setup is a backdoor, with no way of proving it has been disabled. 100% unlike other systems. 3:44 PM – 1 Nov 2016 Source.
The zcash trusted setup is exactly that: trusted. In no way is it trustless. 10:34 PM – 1 Nov 2016 Source.
Later in May, 2017:
Thinkpad T520 I used for the @zcashco trusted setup was 100% vulnerable to this: https://arstechnica.com/security/2017/05/the-hijacking-flaw-that-lurked-in-intel-chips-is-worse-than-anyone-thought/ … See: https://support.lenovo.com/it/en/product_security/len-14963#ThinkPad … 4:19 PM – 8 May 2017 Source.
Just the networking computer, not compute node, so the airgap should have protected the setup. But shows the paranoia was 100% justified. 4:22 PM – 8 May 2017 Source.
Without the airgap the Intel AMT backdoor could have 100% compromised the @zcash trusted setup. 4:22 PM – 8 May 2017 Source.
In response to a tweet: does this change anything in your mind regarding the sanctity of the zcash ceremony?
Yes: an attacker may have compromised the DVD’s, which were burnt and verified on vulnerable laptops. 4:34 PM – 8 May 2017 Source.
I’m going to have to recheck them on a clean computer, and even then it’s a bit dubious: DVD’s are not read-only – can be further burned. 4:34 PM – 8 May 2017 Source.
In response to a tweet: how are you going to recheck the DVDs? I guess it’s possible to backdoor DVD via twin sector method https://en.wikipedia.org/wiki/Compact_Disc_and_DVD_copy_protection#Twin_sectors … 1/2
At minimum finding a few DVD drives without burn capability, and rechecking w/ diverse controlling computes seems like a good idea. 4:56 PM – 8 May 2017 Source.
In response to a tweet: Even then, the ISO could’ve been compromised in subtle ways (specific known-bad libraries for e.g.), or the MPC implementation could be bad.
Yeah, there hasn’t been enough attention paid to that IMO. Although at least that’s stuff that can be determined after the fact. 3:35 AM – 9 May 2017 Source.
In a presentation at Coinbase, Bitcoin Core Developer Greg Maxwell has stated:
“Zcash isn’t unconditionally sound, and cannot be made unconditionally sound with current technologies – not even close. In fact, Zcash requires a trusted setup, meaning that a number of trusted parties have to get together, and if they cheat, they can break the crypto and create unbounded, undetectable inflation. So, if there’s a crypto break, or the trusted setup were broken – very bad news. Now they did a bunch of stuff – in the Zcash altcoin – with having a good ritual to increase trust – that the trusted setup is trustworthy – but they may have to redo this procedure to upgrade the crypto overtime, so it’s a vulnerability.” Source.
In a Twitter discussion regarding the WannaCry ransomware attack and the difficulty of cashing out illicitly-obtained cryptocurrencies to fiat currency, Zcash’s founder and CEO, Zooko Wilcox stated:
And by the way, I think we can successfully make Zcash too traceable for criminals like WannaCry, but still completely private & fungible. … 6:22 PM – 12 May 2017 Source.
… At least for as long as criminals want to cash out to fiat (years? decades?). … 6:23 PM – 12 May 2017 Source.
… I know to techies and ideologues that sounds contradictory or suspect, but I think it’ll work in the real world, at least for now. ៚ 6:25 PM – 12 May 2017 Source.
Later, he backtracks:
How bout we just pretend I never said this. 4:56 PM – 13 May 2017 Source.
- Privacy, Traceability, Linkability
Dash is not cryptographically private whatsoever. Dash promises “privacy” through mixing, utilizing a modified version of CoinJoin – a method initially created to “anonymize” Bitcoins. Dash functions similar to Bitcoin, in that the blockchain is transparent by default, while offering optional privacy by way of mixing. To mix the coins, the “PrivateSend” feature must be employed, which sends the coins through a series of chained CoinJoins. In other words, the PrivateSend feature mixes the coins that are being sent, with other users whose coins are sent through PrivateSend. The more users the coins mix and “chain” with, the “more private” the coins end up.
A server called a “masternode” is required to expedite the mixing process, which in turn “requires users to trust that the server is not recording details on where each user’s outputs are ending up.” A masternode requires a deposit of 1,000 Dash coins to run, which in theory, “prevents someone from creating an arbitrary number of nodes for the purpose of recording CoinJoin details.” Source. However, this does not prevent the potential for an attacker with great means (e.g. a government, or group of hackers) from consolidating masternodes for nefarious purposes. Furthermore, there is nothing preventing these masternodes from logging the user’s output destinations, and there is no way to audit whether or not a masternode is logging anything at all. This threat is further exacerbated by the fact that most masternodes are hosted on a limited range of VPS providers – which presents the possible, unknowable vulnerability of the VPS providers being able to log information without the masternode owner’s consent or awareness. Moreover, from a practical standpoint, the PrivateSend mixing process is liable to take up to several hours or days to complete, depending on the amount of rounds the coins are chosen to mix through.
Dash’s blockchain is transparent and offers a rich list. It is the case that transactions are easily viewable by an observer, and coins which are mixed through the PrivateSend feature end up looking suspicious in comparison to a regular transaction.
- Fungibility
Because Dash’s blockchain is transparent by default, and only optionally utilizes mixing “privacy,” there is the potential for an entity to deny or blacklist Dash coins and addresses.
- Decentralization
Dash offers incentivized nodes called masternodes – a setup required for the PrivateSend feature to function. Not only do masternodes require a deposit of 1,000 Dash coins to run, but masternodes have more power, control and influence over regular nodes. In other words, a limited, affluent group of people consolidate more power and control, therefore Dash is not wholly decentralized.
Furthermore, Dash utilizes a mechanism called “sporks” (multi-phased forks), which allows the Dash development team to update its code and release it to the entire Dash network. Sporks are variables based on different features and functions, meaning that the Dash development team, by way of a private key held by the development team, can arbitrarily enable and disable different features and functions effective to the entire network.
Case in point, on August 30, 2017, a Dash Core Developer announced a potential exploit that would allow an attacker “with 6 or more Masternodes” to perform a double spend or a network fork. In response, the development team remotely disabled the vulnerable feature in question (InstantSend), by way of sporks, to ensure that the attack would not be performed until a fix was released. Source. According to “strategy advisor” Evan Duffield, “this is something you simply can’t do with a hard fork or a soft fork because it’s – it’s [sic] something that the administrators need to… to [sic] have some – some [sic] power over.” – “The – the [sic] only issue with the Sporks is that it’s a singular key. And it’s – it [sic] is controlling a decentralized network.” Source.
As a fallback, Dash has introduced a governance tool called Sentinel, where the maintainers of masternodes are able to vote, and through majority vote, trigger a spork a certain direction. Source. As pointed out by @fluffypony – with the power of sporks, the Dash development team is able to – for example – invalidate the past 24 hours of blocks for the sake of invalidating all transactions in those blocks, opening up the vulnerability for the Dash team to “deposit Dash on an exchange, sell it, and then flip a switch invalidating the deposit under the guise of a ‘fix’.”
Dash is not only dependent on the sporks trusted system, but the private keys that are required to utilize sporks are held by the development team, making Dash centralized.
Furthermore, miners and masternodes are required to split block rewards, with each group earning 45% of coins generated per block. The “Dash Treasury” retains the remaining 10% of coins generated per block, “allocated monthly to any independent contractor or service provider who wants to be ‘hired’ by the network to provide services including programming, marketing, graphic design, or any other services that help improve and promote the Dash currency.” Source.
- Privacy, Traceability, Linkability
Verge is not cryptographically private whatsoever. Verge only offers “privacy” by way of Tor and I2P routing, to obfuscate traffic and conceal a user’s IP address when transacting. Source.There are no cryptographic privacy features with regards to the blockchain, the linkability and traceability of transactions and addresses, nor the concealment of the amounts being transacted. All information, including the destination of transactions and the amounts being transacted, are transparent on the blockchain, and are easily viewable by an observer. Moreover, the privacy, traceability and linkability of transactions and addresses on the Verge blockchain are exceptionally worse than Bitcoin, because the Verge blockchain contains less transactions overall. Furthermore, Verge offers a rich list, thus it is not private at all.
On September 4, 2017, a video was put out (and was then removed and reuploaded by another entity) announcing the implementation of stealth addresses – however, there is no proof that this implementation is underway, nor do stealth addresses provide sufficient privacy, especially when it comes to the traceability of coins and the privacy respective to the amounts being transacted.
- Fungibility
Because of Verge’s transparent blockchain, there is the potential for an entity to deny or blacklist Verge coins and addresses.
- Decentralization
Verge is a Bitcoin clone, and therefore it carries Bitcoin’s attribute of decentralization.